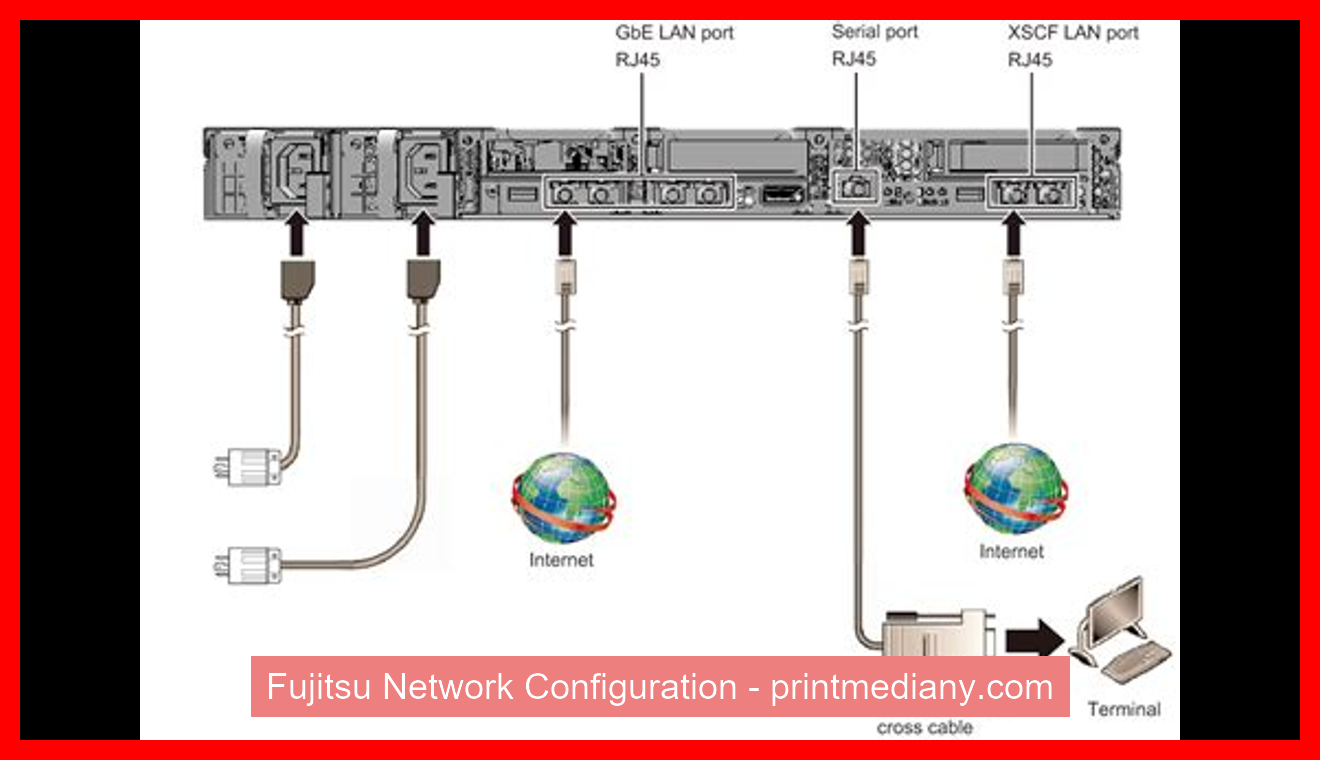
Introduction to Fujitsu Network Configuration
Managing a network can be a complex task, especially in large organizations. It requires a lot of effort to configure and maintain different network components, including routers, switches, firewalls, and servers. Fujitsu Network Configuration is a tool that provides a comprehensive solution to this problem by simplifying the process of network configuration.
Overview of Fujitsu Network Configuration
Fujitsu Network Configuration is an integrated tool that enables network administrators to configure and manage networks effortlessly. It is designed to centralize the management of network devices, allowing administrators to control and monitor the network from a single point. The tool is ideal for organizations that require efficient network management and optimization.
Importance of Network Configuration
Network configuration is an essential aspect of network management. It involves the process of setting up and managing network devices and services, ensuring that they are running optimally. A well-configured network ensures smooth network operations, enhances network security, and improves performance. With Fujitsu Network Configuration, network administrators can automate configuration tasks and reduce the likelihood of configuration errors.
Fujitsu’s Approach to Network Configuration
Fujitsu’s approach to network configuration involves simplifying the process of configuration and management. The company provides an integrated tool that centralizes network management, making it easier for administrators to configure and maintain the network. Fujitsu Network Configuration allows organizations to save time and resources by streamlining network configuration tasks. The tool’s automation capabilities ensure that configuration tasks are carried out efficiently, reducing the likelihood of errors and improving network performance.
Fujitsu Network Configuration Tools
Fujitsu Network Configuration Tools is a suite of software solutions designed to simplify network operations for service providers, data centers, and enterprises. These tools are specifically designed to work with Fujitsu network equipment, ensuring seamless integration and maximum efficiency.
Fujitsu Network Proactnes II
Fujitsu Network Proactnes II is a comprehensive network management system designed to enable network operators to efficiently manage and optimize their networks. This tool provides end-to-end network visibility and control, enabling operators to quickly identify and resolve issues before they impact network performance.
Fujitsu Virtuora Network Controller
Fujitsu Virtuora Network Controller is a software-defined networking (SDN) controller that enables network administrators to automate the configuration, provisioning, and optimization of their networks. This tool helps to reduce network complexity and increase agility, allowing operators to rapidly respond to changing network requirements.
Fujitsu Virtuora Service Orchestrator
Fujitsu Virtuora Service Orchestrator is an orchestration platform that enables network operators to automate the delivery of network services. This tool simplifies service deployment and management, allowing operators to rapidly deliver new services and scale existing services as needed.
Fujitsu Network Densified Ethernet Switches
Fujitsu Network Densified Ethernet Switches are a family of high-density switches designed for data center and cloud environments. These switches provide high-performance, low-latency connectivity for both east-west and north-south traffic, enabling data centers to deliver the low-latency, high-bandwidth connectivity that modern applications require.
Read more:
- Fujitsu Network Parts: High-Quality Parts for Efficient Network Performance
- Fujitsu Network Accessories – Enhance Your Network Performance
- Fujitsu Network Warranty: Reliable Coverage for Your Network Infrastructure
Fujitsu Network Smart Lambda Controller
Fujitsu Network Smart Lambda Controller is a software-defined optical networking (SDON) controller that enables service providers to automate the configuration, provisioning, and optimization of their optical networks. This tool helps to reduce network complexity and increase agility, allowing service providers to quickly provision new services and scale existing services as needed.
Configuration Management Strategies
Configuration management is an essential practice that ensures consistency, reliability, and integrity of software and hardware systems. It involves managing changes made to systems and keeping track of configuration changes.
Automated Configuration Management
Automated configuration management is the process of automatically managing and deploying configuration changes using specialized software tools. This strategy is highly efficient, cost-effective, and minimizes human error.
Manual Configuration Management
Manual configuration management is a process that involves manually configuring and tracking software and hardware systems. This approach is time-consuming, prone to errors, and can lead to inconsistencies in system configuration.
Configuration Backup and Restoration
Configuration backup and restoration is an essential strategy that involves backing up system configurations so that they can be restored in case of failure or loss. This strategy ensures system availability and minimizes downtime.
Fault Management Strategies
Effective fault management is essential for ensuring network stability and avoiding costly downtime. Fault management strategies consist of a set of procedures that network administrators follow to detect, isolate, and correct faults that occur in a network.
Root Cause Analysis
Root cause analysis is a methodical approach to troubleshooting that involves identifying the underlying cause of a network outage or performance issue. This involves analyzing data from multiple sources and using a variety of tools and techniques to pinpoint the root cause of the problem. Once the underlying cause has been identified, network administrators can implement corrective actions to prevent similar issues from occurring in the future.
Alarm Correlation
Alarm correlation involves analyzing multiple network alarms to determine the root cause of a particular issue. This process involves collecting data from a variety of network devices and services, and then aggregating and correlating the information to identify the root cause of the problem. Alarm correlation can help network administrators quickly identify the critical alarms that require immediate attention, and prioritize their troubleshooting efforts accordingly.
Performance Monitoring
Performance monitoring involves tracking key performance metrics, such as bandwidth utilization and packet loss rates, to detect issues before they become critical. By regularly monitoring performance metrics, network administrators can identify trends and proactively address potential issues before they impact network performance.
Security Management Strategies
Effective security management strategies are critical to protecting an organization’s sensitive data, intellectual property, and reputation. These strategies involve implementing various security measures, such as:
Network Access Control
Network access control (NAC) is a security solution that restricts user access to a computer network. Using NAC, organizations can control which devices and users can connect to their network. NAC also allows organizations to monitor network activity, enforce security policies, and respond to security incidents.
Firewalls and Intrusion Detection/Prevention Systems
Firewalls and intrusion detection/prevention systems (IDS/IPS) are essential security solutions that help prevent unauthorized access to a network. Firewalls act as a barrier between a trusted internal network and untrusted external networks, while IDS/IPS detect and respond to network-based threats.
Encryption and Authentication
Encryption and authentication are critical components of a security management strategy. Encryption involves scrambling data so it can only be read by those with the proper authorization. Authentication involves verifying the identity of users and devices before granting access to a network. Together, encryption and authentication help ensure that only authorized users can access sensitive data.
Integration with Other Network Management Tools
Fujitsu Network Integration with OpenStack
Fujitsu Network provides integration with OpenStack, an open-source cloud computing platform. This integration allows for a simplified and efficient management of network resources, as well as the ability to easily provision and manage virtual networks.
Integration with Network Operations Center (NOC) Tools
Fujitsu Network also offers integration with common Network Operations Center (NOC) tools such as SolarWinds and Nagios. This integration allows for real-time monitoring of network devices, as well as alerts and notifications for any potential issues.
Integration with Security Information and Event Management (SIEM) Tools
Fujitsu Network can also be integrated with popular Security Information and Event Management (SIEM) tools like Splunk and QRadar. This allows for the collection and analysis of network security information, as well as the ability to quickly respond to any detected security threats.
Best Practices for Fujitsu Network Configuration
Regular Audits and Assessments
Regular audits and assessments are the cornerstone of a successful network configuration strategy. By conducting regular audits to ensure that configurations are up-to-date and that there are no errors or vulnerabilities in the configurations, IT teams can ensure that their network is secure, reliable and scalable. These assessments should be conducted by experienced professionals who are familiar with the network configuration, and who can make recommendations for improvement based on best practices.
Centralized Management
Centralized management is an important best practice for Fujitsu network configuration. With centralized management, all network configurations are managed from a single location, making it easy to monitor and manage network activities, troubleshoot issues and ensure consistency across all devices. This approach can help reduce the complexity of network management, improve network visibility and control, and optimize network performance.
Use of Standard Templates
The use of standard templates is another best practice for Fujitsu network configuration. With templates, IT teams can create and standardize network configurations, making it easy to replicate configurations across multiple devices. By adopting a template-based approach, IT teams can reduce the time and effort required to configure devices, improve network consistency, and ensure that configurations adhere to best practices and industry standards.
By following these best practices for Fujitsu network configuration, IT teams can ensure that their network is secure, reliable and optimized for business performance.
Challenges in Fujitsu Network Configuration
Complexity of Networks
One of the major challenges in Fujitsu network configuration is the complexity of networks. Networks are becoming increasingly complex with the addition of new devices, applications, and services. This can make it difficult for network administrators to keep track of everything and ensure that the network is running smoothly. The complexity of networks also makes it more difficult to diagnose and troubleshoot issues.
Lack of Standardization
Another challenge in Fujitsu network configuration is the lack of standardization. Different vendors may use different protocols, interfaces, and configurations, making it difficult to integrate different devices and services into a single network. This can also create compatibility issues and increase the risk of errors and downtime.
Emerging Security Threats
Fujitsu network configuration is also challenged by emerging security threats. As networks become more complex and interconnected, they also become more vulnerable to attacks. Hackers and other malicious actors are always looking for vulnerabilities to exploit, and network administrators must constantly be on guard to protect their networks and data.
Future Trends in Fujitsu Network Configuration
Greater Automation and Self-Configuration
In the future, we can expect to see a significant increase in automation and self-configuration capabilities within Fujitsu network configuration. This will enable networks to automatically maintain and optimize themselves, reducing the need for manual intervention and minimizing the risk of human error.
Integration with Artificial Intelligence and Machine Learning
The integration of artificial intelligence and machine learning is another imminent trend that we can expect to see within Fujitsu’s network configuration. These technologies will enable networks to analyze data and make decisions based on that analysis, improving their performance and making them more efficient.
Enhanced Security through Blockchain Technology
The use of blockchain technology is also expected to increase within Fujitsu’s network configuration in the future. Blockchain technology provides a highly secure and transparent way to store and share data, making it an ideal solution for protecting sensitive network information.
In conclusion, the future of Fujitsu network configuration is likely to involve greater automation and self-configuration capabilities, integration with artificial intelligence and machine learning, and enhanced security through blockchain technology. These trends are expected to improve the performance, efficiency, and security of Fujitsu’s networks and help them stay at the forefront of the industry.
The Importance of Effective Network Configuration
Network configuration is a critical aspect of modern network management. With the proliferation of devices, applications, and data on networks, it’s important to ensure that all the pieces fit together seamlessly. Proper configuration ensures that information is transmitted accurately, securely, and efficiently, without loss or corruption.
Fujitsu’s Tools and Strategies to Better Configure, Manage, Secure and Optimize Networks
Fujitsu is helping organizations to better manage their networks through its innovative tools and strategies. Its tools enable administrators to quickly and easily configure the network, ensuring that it’s optimized for maximum efficiency and security. The company’s strategies help businesses to stay ahead of potential threats by identifying vulnerabilities and mitigating risks before they become problems.
The Increasing Importance of Effective Network Configuration
As network complexity and security threats continue to increase, the importance of effective network configuration will only become more pronounced. The consequences of poor configuration can be catastrophic, including data loss, downtime, and breaches. For businesses that rely on networks to operate, effective configuration is essential to ensure success and continuity.
In conclusion, Fujitsu’s network configuration tools and strategies are a valuable asset to organizations seeking to optimize their networks and stay ahead of potential threats. As network environments become more complex and the need for security intensifies, effective configuration will become more important than ever.
